EMBOLDENED FRAUDSTERS HAVE LEAPFROGGED FROM SINGLE HOSPITALS TO EXTENSIVE SYSTEMS
MedStar Health Inc., the Maryland-based healthcare provider that operates 10 hospitals and employs approximately 30,000 people, suffered a crippling ransomware attack in late March that was so devastating it not only forced all of its hospitals to revert to paper documentation, but idled electronic record systems and prevented patients from booking appointments.
The MedStar Health attack comes on the heels of two other recent cases involving ransomware directed at similar but smaller healthcare providers. In these cases, both Methodist Hospital in Kentucky and Hollywood Presbyterian, a Los Angeles-based hospital owned by CHA Medical Center of South Korea, were each held hostage within the last two months by a particular form of malware called Locky. While Hollywood Presbyterian decided to pay its attackers a ransom and the Kentucky hospital did not, each case and others like it signal the troubling arrival of an effective brand of cyber extortion uniquely susceptible to healthcare.
Lucrative Returns Make Healthcare a Target
It should come as no surprise that privacy data such as protected health information is increasingly viewed as a new form of currency to enterprising cyber criminals bent on identity theft and other fraud. In recent years, cyber attacks against companies such as Anthem, Community Health Systems, and Premera Blue Cross, have served as a testament to this, while also highlighting the requirement for these companies to mature their cybersecurity beyond the standard if they are serious about escaping regulatory penalties and the accompanying havoc to their business operations.
But the industry is targeted for reasons that go beyond the inherently lucrative nature of patient privacy data on the black market. With the advent of Locky and other Cryptolocker-type malware targeting the industry, attackers understand the criticality with which medical providers require timely and uninterrupted access to essential systems and records. After all, if an attack locks up a physician’s ability to access critical data like a patient’s medical or drug history, the delivery of urgent care on their behalf may be impeded. And some hospital administrators, already weary of lawsuits by litigious patients, are opting to shell out as a result, further emboldening these criminals and all but inspiring others to get in on this bankable game as well.
The Pervasiveness of Ransomware
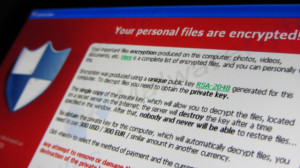
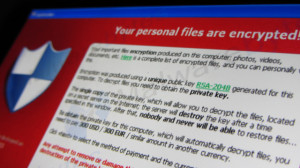
Ransomware can take various forms but the more prevalent variety are malware such as Locky, which is part of the Cryptolocker genus and designed to target the victim’s back-up folders while forcing them to pay a Bitcoin ransom before being provided a special decryption key to retrieve their files and systems. Having initially targeted individuals or small businesses, sophisticated variants such as Locky have graduated to encrypting and locking entire network servers, thereby preventing users at the enterprise level from accessing shared files and databases.
The FBI says ransomware attacks such as these have increased so sharply that companies have already paid more than eight times in ransomware payments so far in 2016 than they did in all of 2015.
Ways to Avoid Victimhood
Unfortunately, for those organizations victimized by such ransomware, the options to retrieve stolen data and regain access are very limited. As some cybersecurity professionals and the FBI recommend, companies must either pay their ransom – despite the ethical ramifications of doing so – or retrieve their data from back-ups. Short of those two options, there is very little left to do. While it might seem obvious, it is important to remember that the fundamental business model of ransomware is predicated on an organization’s willingness to pay. By routinely and securely backing up data, systems, and configurations, to include of course maintaining copies that are kept offline, proactive organizations take the power away from their extortionists and may avoid the pitfalls of such victimhood in the first place.
In addition to backing up systems, simple practices such as patching regularly, keeping preventative controls like antivirus and firewalls both up to data and properly configured, and blocking potentially dangerous ZIP files are crucial as well. Secure Halo further encourages healthcare organizations and other companies to adopt additional (and basic) best practices to better prepare and prevent such threats in this new landscape:
Conduct Security Awareness Training. By now, corporate risk managers and other enterprise security leaders understand the adage of being only as strong as the weakest link. With the rise of phishing attacks as well as the use of popups by cyber criminals to spread malware, recognizing threats and preventing accidental clicks becomes crucial. In addition to solutions such as popup blockers and spam filters, a culture of security must be created that instills a sense of skepticism at the user level that aims to defeat the increasingly clever ways in which adversaries are using social engineering to trick well-intentioned employees. Some solutions might include simulated phishing attacks and other training.
Understand Risk Tolerance. As Secure Halo constantly reiterates, the objective of any effective risk management plan – no matter the industry – should be to anticipate threats to an enterprise based on an assessment of its unique threat profile and an understanding of why determined adversaries might target it in the first place. From there, a preventative and proactive strategy should be implemented that incorporates holistic security controls across multiple domains, such as data, physical and mobile security, internal and external business operations, and insider threat.
Create a Business Continuity Plan. Business continuity plans are essential features of a corporate risk management plan. Simply put, it provides companies with fundamental capabilities needed to reduce the cost of a cyber incident by preserving their access to critical business information and assets. For healthcare organizations to survive the potentially disastrous consequences of ransomware such as Locky, the ability to recover and to return to normal functioning as quickly as possible is paramount. As such, these organizations must categorize both their information and systems based on their criticality to operations and they must determine appropriate risk tolerance levels for these assets accordingly. Once that is understood, they should develop processes which then must be incorporated into a written business continuity plan and executed with confidence should something as dreadful as ransomware occur.
As we at Secure Halo are fond of saying, while it may be impossible to completely prevent sophisticated cyber attacks using Cryptolocker-type malware, it is essential for organizations to understand that the scope of victimhood will always be a function of an organization’s preparedness.
Contact TSC for more information on ransomware or for help to develop impactful strategies to reduce the impact of cyber extortion on your enterprise.